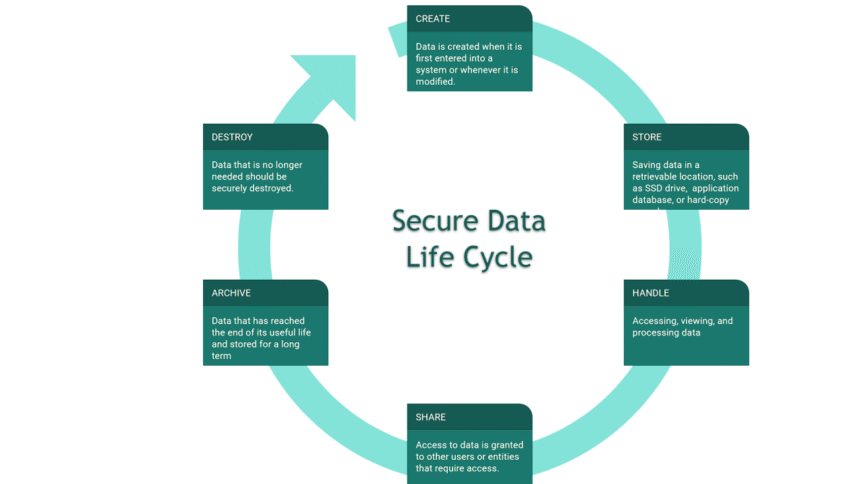
In the digital age, protecting business data is paramount. From client information to proprietary assets, companies must be proactive in safeguarding their digital resources. While many focus on security during daily operations, the lifecycle of IT assets, from acquisition to disposal, is equally critical. Technology Lifecycle Management (TLM) plays an essential role in ensuring data remains protected throughout its lifespan. This article explores how TLM contributes to enhanced data security by focusing on key stages and effective practices for managing IT assets.
What is Technology Lifecycle Management (TLM)?
Technology Lifecycle Management is the process of managing IT assets from their inception to their retirement. This includes the stages of planning, acquisition, deployment, maintenance, and eventual end-of-life (EOL) disposal. By systematically overseeing each stage of an IT asset’s life, businesses can ensure their infrastructure remains secure, compliant, and optimized for performance. Proper management of technology helps minimize risks and prolongs the useful life of assets, all while maintaining security standards.
How TLM Enhances Data Security
Data security is a consistent concern at every stage of an IT asset’s lifecycle. From choosing the right equipment to ensuring proper disposal, each phase offers opportunities to strengthen security measures.
Acquisition and Initial Setup
The security journey begins with the acquisition of IT equipment. When selecting devices, businesses must prioritize security features such as encryption capabilities, secure boot options, and robust user access controls. During the initial setup phase, implementing firewalls, antivirus software, and secure network configurations helps mitigate risks from the start. Properly configuring systems ensures that vulnerabilities are minimized before deployment. It is important to keep track of assets such as computing and mobile devices like laptops and tablets, data and networking equipment such as servers, HDDs, and SSDs, and other electronics.
Deployment and Ongoing Usage
When deploying IT assets across the organization, businesses must ensure that systems are properly configured to prevent security lapses. Regular software updates and patch management are essential to close security gaps and protect against cyber threats. Implementing comprehensive policies for device usage and data handling can further bolster security. Regular audits of systems help identify and resolve vulnerabilities before they escalate into major issues. Businesses should also enforce strong access control policies and ensure that only authorized personnel can access sensitive data.
Maintenance and Proactive Monitoring
Security requires ongoing attention. Regular maintenance of IT systems includes monitoring for suspicious activities, performing vulnerability assessments, and patching systems against newly discovered threats. Additionally, providing employees with continuous security training helps minimize the risk of human error, a significant contributor to data breaches. Continuous monitoring of assets allows businesses to proactively address potential issues before they compromise sensitive information.
End-of-Life (EOL) Disposal
When an IT asset reaches the end of its useful life, businesses are particularly vulnerable to data breaches. Improper disposal of devices can leave sensitive data exposed, even if the equipment is no longer in use. It is vital to ensure all data is thoroughly wiped or destroyed before equipment is discarded. Data destruction methods like encryption, data wiping tools, and physical destruction (e.g., shredding hard drives) help eliminate the risk of data recovery. Partnering with certified IT asset disposition (ITAD) services ensures that data destruction complies with industry standards and regulations, safeguarding businesses from potential breaches during disposal.
Best Practices for TLM to Strengthen Data Security
To effectively manage the security of IT assets throughout their lifecycle, businesses should adopt a few key practices:
- Develop a Comprehensive Technology Policy
A clear technology policy is the foundation of TLM. This policy should outline security standards for asset configuration, user access control, data storage, and more. Regular updates to the policy ensure businesses stay compliant with evolving security requirements and best practices. - Implement Secure Data Sanitization
Before retiring or selling old devices, it’s crucial to ensure that no sensitive data remains on the equipment. Using secure data sanitization methods, such as data wiping software or physical destruction, guarantees that no information can be retrieved. By eliminating the risk of data recovery, businesses protect themselves from potential breaches. - Partner with Certified ITAD Providers
Working with certified secure IT asset disposition services ensures that businesses follow proper procedures for disposing of outdated technology. These services not only provide secure data destruction but also help businesses meet regulatory requirements for data privacy and environmental responsibility. By relying on a certified ITAD provider, businesses can ensure that their EOL processes are both secure and compliant. - Conduct Regular Audits and Assessments
Frequent audits and assessments help ensure that IT assets remain secure throughout their lifecycle. These audits assess the configuration, maintenance practices, and usage of devices, identifying any areas that need attention. Regular risk assessments also help businesses stay ahead of emerging threats and vulnerabilities. - Ongoing Employee Education and Training
Human error is a major cause of data breaches. To mitigate this, businesses should prioritize ongoing security training for employees. Educating employees about recognizing phishing attempts, safe data handling, and secure IT practices reduces the risk of internal vulnerabilities. A well-informed workforce is a key component of a secure IT infrastructure.
The Role of ITAD Services in Data Security
What Are ITAD Services?
IT asset disposition (ITAD) services specialize in the secure destruction and recycling of outdated or unwanted technology. These services handle the entire process, from wiping data to ensuring devices are responsibly recycled. ITAD providers are experts in compliance, offering businesses the reassurance that their IT asset disposal follows data protection laws and environmental regulations.
Benefits of ITAD Services
Certified ITAD providers offer several key benefits that enhance data security and environmental responsibility. They ensure that data is fully destroyed or securely wiped, preventing unauthorized access. Additionally, ITAD services adhere to e-waste recycling regulations, ensuring that hardware is disposed of in an environmentally responsible manner. By relying on certified ITAD services, businesses can be confident that their technology lifecycle management is both secure and compliant.
Conclusion
Technology Lifecycle Management plays a pivotal role in maintaining robust data security throughout the lifespan of IT assets. From acquisition to disposal, each stage offers an opportunity to implement security measures that minimize risks and protect sensitive information. By adopting best practices like data sanitization, regular audits, and partnering with certified ITAD providers, businesses can enhance the security of their IT assets and ensure compliance with industry regulations. Proactive management of IT assets not only protects business data but also extends the useful life of technology, providing long-term value and security for organizations of all sizes.