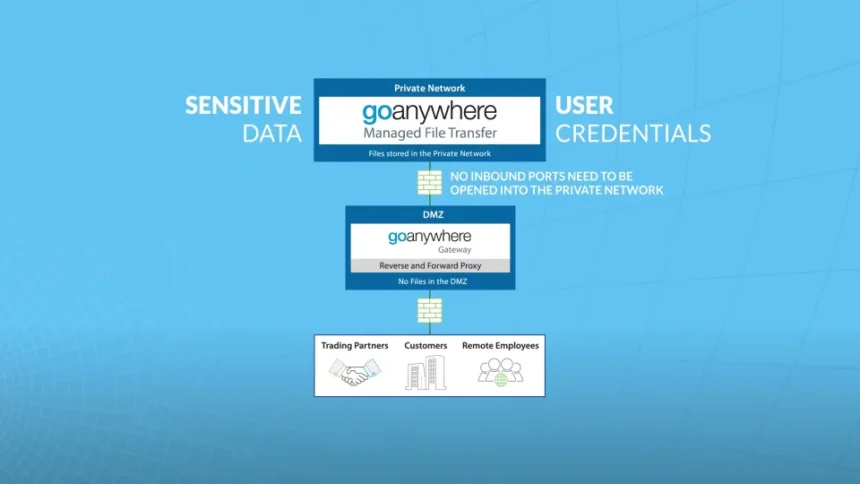
In the digital era, where data breaches are increasingly common and costly, businesses must ensure the security and integrity of their data transfers. Managed File Transfer (MFT) Gateways, also known as Secure File Gateways, are critical components that safeguard sensitive information as it moves in and out of an organization. This article explores the essential features of MFT Gateways that enhance data security, offering robust protection against a range of cybersecurity threats.
- Comprehensive Encryption
One of the fundamental features of a secure file gateway is comprehensive encryption. Data must be encrypted at rest and in transit to protect against unauthorized access and interception. MFT Gateways use advanced encryption standards, such as AES (Advanced Encryption Standard) with 256-bit keys, ensuring that data is unreadable to anyone without the proper decryption key. This level of encryption is crucial for complying with regulatory requirements and safeguarding sensitive information such as financial records, personal data, and intellectual property.
- Authentication and Authorization
Effective MFT Gateways implement stringent authentication and authorization measures to ensure that only authorized users can access the system. This typically involves multi-factor authentication (MFA), which requires users to provide two or more verification factors to gain access, adding an extra layer of security beyond just usernames and passwords. Additionally, role-based access control (RBAC) is another critical feature, limiting user access based on their role within the organization. This minimizes the potential damage from insider threats and reduces the risk of accidental data exposure.
- Auditing and Reporting
To maintain high security standards, MFT Gateways provide detailed auditing and reporting capabilities. These systems log every file transfer attempt, success, and failure, along with timestamps and user details. This not only helps in monitoring and detecting suspicious activities but also supports compliance with various data protection laws that require detailed records of data transactions. Regular reports generated by the secure file gateway can help identify patterns that may indicate a security breach or inefficiencies in the file transfer process.
- Automated Security Policies
Another essential feature of MFT Gateways is the ability to implement and manage automated security policies. These policies can dictate how data is handled, ensuring consistency and compliance with corporate security protocols and legal requirements. For example, a policy might automatically encrypt all outgoing files or block transfers containing sensitive information to unauthorized destinations. Automating these decisions reduces the reliance on human intervention, decreasing the likelihood of errors and enhancing overall security.
- High Availability and Disaster Recovery
For businesses that rely heavily on the uninterrupted availability of data, the secure file gateway must include features that support high availability and effective disaster recovery. This means the gateway should be deployable in a redundant configuration across multiple physical or cloud-based servers to ensure continuous operation during hardware failures or maintenance periods. In addition, robust disaster recovery capabilities ensure that data can be quickly restored after any data loss event, whether due to technical failures, natural disasters, or cyber-attacks.
Conclusion
MFT Gateways are vital for businesses seeking to protect their data transfers from growing cybersecurity threats. By incorporating features like comprehensive encryption, robust authentication, detailed auditing, automated security policies, and high availability, these gateways provide a secure infrastructure that can defend against both external and internal security risks. Investing in an advanced secure file gateway not only helps in safeguarding valuable information but also ensures that businesses can operate with confidence in their data security measures.