In the modern digital world, any business depends on technology to conduct its business effectively, keep confidential data, and communicate with its clients. However, such reliance also provides a path to cyber threats that are changing at an alarming speed. No organization is immune, regardless of whether it is a small start-up or a multinational organization. These challenges must be proactively and holistically approached to cybersecurity, that is, integrated with strategy, technology, and awareness, in order to be ahead of them.
Developing a Culture of Security Consciousness.
People in an organization are the first line of defense, which is not necessarily a piece of software. The daily operations of employees include data, email, and access to networks, so it is no wonder that they are an important target of cybercriminals. Employee education about how to identify suspicious messages, how to prevent unsafe downloads, and powerful passwords might reduce the risk of breach considerably.
This is not just about training them at least once a year in order to establish a culture of security awareness. It needs constant reminders, available materials, and leadership that must take cybersecurity seriously. Employees who realize that their activity directly affects the safety of the systems of the company become active defendants, instead of the possible weak links.
Defending with the New Benefits.
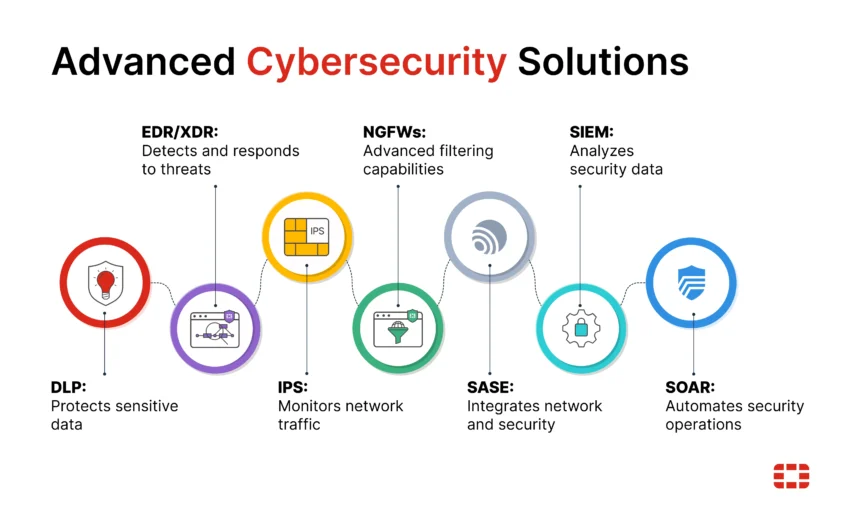
It is no longer needed to use a single tool or solution in the complex cyber environment. Rather, companies are implementing a defense-in-depth approach or defense in layers. This is a model that integrates firewalls, intrusion detection systems, endpoint protection, and encryption to form several barriers to unauthorized access.
Adoption of clouds also brings more complexity. Although cloud providers have strong security, business owners must secure their data and applications. Multi-factor authentication and secure access controls are tools that are important in minimizing exposure. Combined intelligently, these measures can make sure that when one barrier collapses, there is another one that will prevent or delay an attacker.
Real-time Monitoring and Responding.
Prevention is not the only thing, and detection and response are equally vital. The threats may sometimes be able to beat even the best defenses, and hence, continual monitoring is a requirement. Threat detection tools are real-time, and they monitor unusual activity, including unauthorized logins or abnormal data transfers, and provide a warning to security teams before things go out of control.
An incident response plan, which has been prepared previously, is the difference between a small inconvenience and a significant crisis. This plan must give specific guidelines on how the threats will be identified, contained, and eliminated, and provide communication to stakeholders. Response immediately will reduce harm, save face, and more effectively reestablish operation.
Using Professional Expertise.
Cybersecurity management can be daunting to many businesses, particularly small businesses that lack major in-house IT teams. The threat environment is dynamic, and to keep up with it, one needs expertise. Here is where the outside partners can really assist. Using managed cybersecurity services, companies can access expertise, advanced tools, and 24/7 monitoring, which would otherwise be unavailable to them. This proactive service enables a business to concentrate on growth and innovation with the knowledge that they are leaving its defense in the hands of professionals.
How to Plan to Secure the Future of Cybersecurity.
With digital transformations gaining momentum, the understanding of cybersecurity needs to develop as well. The emergence of artificial intelligence, automation and the IoT is a new opportunity–and a new threat. Moreover, hackers are beginning to use AI to develop more realistic phishing or automate the attack, and businesses are using the same technology to enhance defenses and foretell attacks before they happen.
Cybersecurity futurizing implies taking into account such shifts and investing in scaled and flexible solutions. Better still, they will not lose the trust of the customers and partners in a world where the level of trust in the safety of data is turning into a matter of life and death.
Conclusion
Modern business cybersecurity is no longer a necessary investment, but a significant pillar of long-term success. The combination of human, layered, real-time, professional, and proactive preparation is the best solution. Threats will continue to evolve, but the currently existing businesses that specialize in security will not just defend themselves but also establish resilience in the future.