Post Preview
Patch management is a critical yet often underappreciated component within the intricate web of cybersecurity protocols. This vital aspect of vulnerability management involves the timely distribution and installation of software updates, which are crucial to strengthening an organization’s defense mechanisms against cyberattacks. The commitment to this often routine task forms a robust barrier against the exploitation of known security gaps. Understanding, executing, and refining the patch management process can be the difference between a secure network and a compromised one.
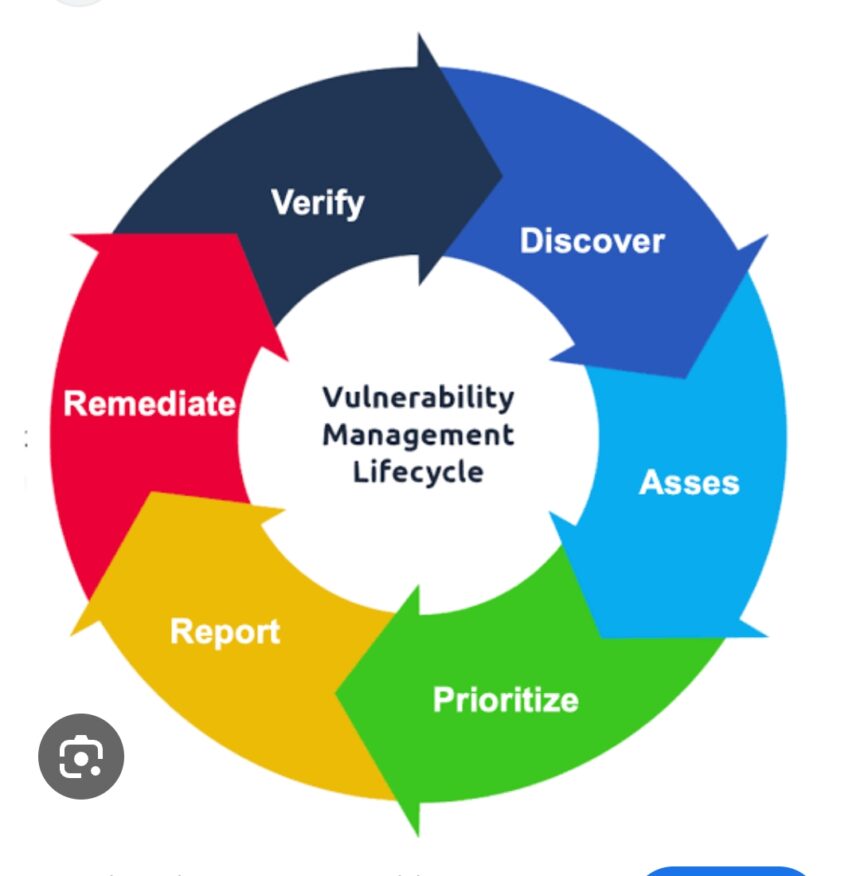
Understanding Patch Management in Vulnerability Life Cycle
Patch management’s role in an organization’s vulnerability lifecycle cannot be overstated. It begins with detecting vulnerabilities and extends to deploying the patches designed to address them. It is a meticulously organized undertaking involving coordination across various IT systems and departments. The systematic deployment of patches safeguards the infrastructure and keeps systems operational. However, given the precise nature of cyber threats, this process must be executed quickly and accurately to maintain cyber resilience effectively.
The Ripple Effect of Neglected Patches
A singular unpatched system can be the starting point for a security breach with far-reaching consequences. There is an inherent danger in complacency; a delayed response to patch releases amplifies the likelihood of security breaches. These lapses in patch management can have a cascading effect, leading not just to isolated incidents but to mass exploitation of the network’s vulnerabilities. The ramifications extend beyond the digital domain, affecting an organization’s integrity, legal standing, and stakeholder confidence.
Strategies for Effective Patch Management
The strategies employed for effective patch management are complex and multifaceted. Successful patch management often involves an analysis of deployment priority — determining which patches should be rolled out first based on threat severity and system criticality. A staged rollout, often starting with a controlled environment before a wide-scale deployment, mitigates the risk of updates causing system issues. In addition, organizations should integrate feedback mechanisms to measure the impact of the patch management process and learn from each deployment cycle.
Automation in Patch Management
One of the more progressive strategies is incorporating automation into patch management. With the advent of sophisticated IT tools, organizations can now automate the more mundane aspects of this process, improving efficiency and reliability. Automated systems can identify the need for patches, test their viability, and deploy them across various environments with minimal manual oversight. This shift towards automation enables organizations to maintain up-to-date systems while redirecting vital IT resources to strategic initiatives that fortify their security posture.
Best Practices in Patch Management
Several best practices in patch management enhance the security of an organization’s IT infrastructure. Conducting regular vulnerability assessments to identify areas needing immediate attention is one such practice. Another is maintaining an inventory of all systems and applications to match every asset. Companies also need to have clear policies for regular systems backup before applying patches to avoid data loss in case of patch-related failures. Employee awareness about the importance of updates is equally important, as human error is often a weak link in security chain.
The Pivotal Role of Patch Management in Security Posture
An effective patch management program is a testament to an organization’s security culture and stance. It is a proactive measure that anticipates threats rather than reacts to them post-exploitation. The commitment to a rigorous patch management system communicates to stakeholders, clients, and competitors that an organization prioritizes its cybersecurity responsibilities. It also prepares an organization for audits and compliance with various regulatory frameworks, ensuring business processes are not hindered by avoidable security concerns.
Conclusion
In the broader scope of vulnerability management, patch management is a stalwart guard against potential cyber threats and reflects a proactive cybersecurity philosophy. While the process may seem daunting, the price of overlooking such a crucial aspect of security far outweighs the investment in its proper management. By adhering to best practices, harnessing the power of automation, and educating the workforce, organizations can effectively manage their patch processes and defend against the ever-present threat of cyberattacks.